Excitement About Managed It Services For Law Firms
A Biased View of It Services Melbourne
Table of ContentsThe Single Strategy To Use For Managed It Services For Law FirmsSome Known Facts About Managed It Services For Law Firms.5 Simple Techniques For Managed It ServicesTop Guidelines Of Managed It Services Melbourne
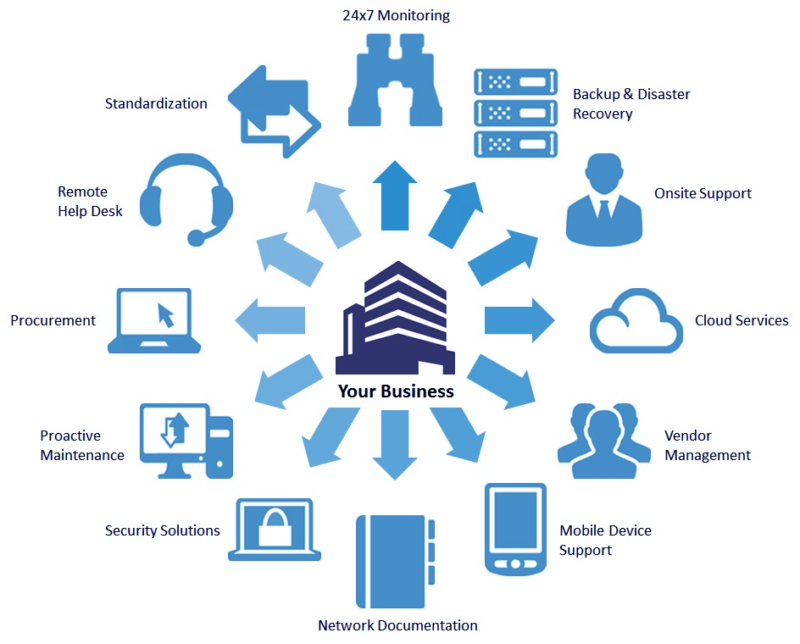
As foresaid, IT sustain offers end-to-end managed IT services, that include these primarily: An IT framework has a variety of laptop computers, workstations, printers, servers as well as hardware systems. A tiny damage or break down may end up in a wonderful loss, which might be of crucial information or details. This taking place eventually influence on the business's returns and also connection.These plans have multi-factor verification, preventing out of the state logins and also several various other ones in a fantastic function. This is extremely for the business that enable staff members to use their own phones for performing tasks. This bring-your-own-device (BYOD) is not every usual, but still exists. The support providing firms put their team to secure that information as well as assets from hackers or misuse.
It ensures that just safe gadgets will have the ability to carry out from another location, as they would be capable of safeguarding the sensitive data of the firm. It describes the on-demand schedule of computer system sources, including information storage and also computer power. This happening does not call for any type of straight energetic management by the customer.
As its advantages are impressive, a lot more and extra companies have actually begun shifting to the cloud for hosting their information. managed it services melbourne. For keeping their secret information concerning consumers and also their customer experience (CX) risk-free, it comes with some phenomenal safety attributes. The tech assistance team manages it well in 2 means: Making sure configuring and taking care of the cloud system for holding a variety of requisite applications, data administration, IT sustain and downtime, Using the full safety and security to what comes under the handled IT solutions from cyber lawbreakers.
8 Simple Techniques For Managed It Services

Something went incorrect. Wait a minute as well as try once again Try once again.
Organizations are increasingly relocating their IT infrastructures right into the cloud (it services melbourne). Many enterprise organizations now run in multi-cloud environments or make use of hybrid on-premises and also cloud-based IT styles. These complexities necessitate the need for IT sustain services to handle these systems. Cloud computer support is an IT solution that aids companies handle their cloud-based facilities.
The Single Strategy To Use For It Service Melbourne
Information back-up as well as recovery assistance include the execution of information backup solutions, such as cloud-based, disk-based and also tape-based back-ups. Data backup as well as recovery assistance likewise entails testing information healing remedies to make sure that they are reliable as well as effective in case of a data loss or corruption. IT sustain is crucial for organizations that rely greatly on their data, such as those in the medical care as well as money industries - managed it services melbourne.
Office technology alters quickly and also gets much more complicated by the year. Whereas the bulk of job-related computer as soon as took area within the workplace wall surfaces and inside a safe boundary, today's dispersed labor force performs service from residences, coffeehouse, autos literally anywhere with web access. Sustaining and also safeguarding the More Info myriad tools and also accessibility factors employees now rely upon to remain efficient has created a whole lot even more job for IT groups that frequently are currently spread as well thin.
Organizations rely on handled providers (MSPs) for a range of reasons, but most frequently, they are utilized by companies without inner IT team or those that want to utilize their internal IT professionals to focus on particular efforts instead of functional obligations for managing modern technology. MSPs give a huge series of services from the essentials such as help workdesk assistance and keeping IT devices and also solutions working right up to supplying the full collection of IT capabilities, i loved this including cyber security, net connectivity, application assistance, information backups, as well as disaster recuperation.

The Single Strategy To Use For It Service Melbourne
Managed IT solutions are much from one-size-fits-all, so partnering with an MSP that recognizes your company and is actively purchased helping you fulfill your objectives is essential.
Potential hazards outside the network are stopped, making sure that an organization's sensitive data continues to be inside. Organizations can go better by specifying extra interior boundaries within their network, which can give improved protection as well as accessibility control. Gain access to control specifies the individuals or teams as well as the devices that have access to network applications as well as systems thereby rejecting unsanctioned gain access to, as well as perhaps hazards.
A vulnerability is a weakness for instance in a software application system and also an exploit is an assault that leverages that vulnerability Source to acquire control of that system. Sandboxing observes the documents or code as they are opened up and looks for malicious behavior to avoid dangers from obtaining on the network. Malware in documents such as PDF, Microsoft Word, Excel and also Power, Factor can be safely identified and blocked before the files reach an unsuspecting end customer.